In 2021, a hacker compromised private information from over 50 million T-Mobile customers. But this story was not an outlier. 2021 was a record-breaking year in data breaches across the United States.
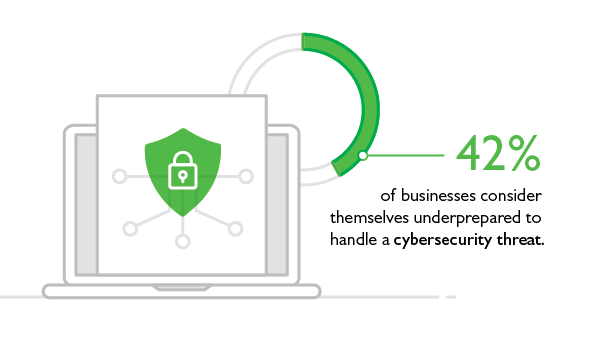
Large and small businesses affected by such attacks may not have the financial resources to combat them. Only one-third of businesses have a cyber insurance policy, according to a survey conducted by the Insurance Information Institute (III).
Online attacks are not going away anytime soon. But banks and other financial institutions offer cyber liability insurance to help protect businesses and individuals. Here’s a rundown of what business owners should know about cyber insurance:
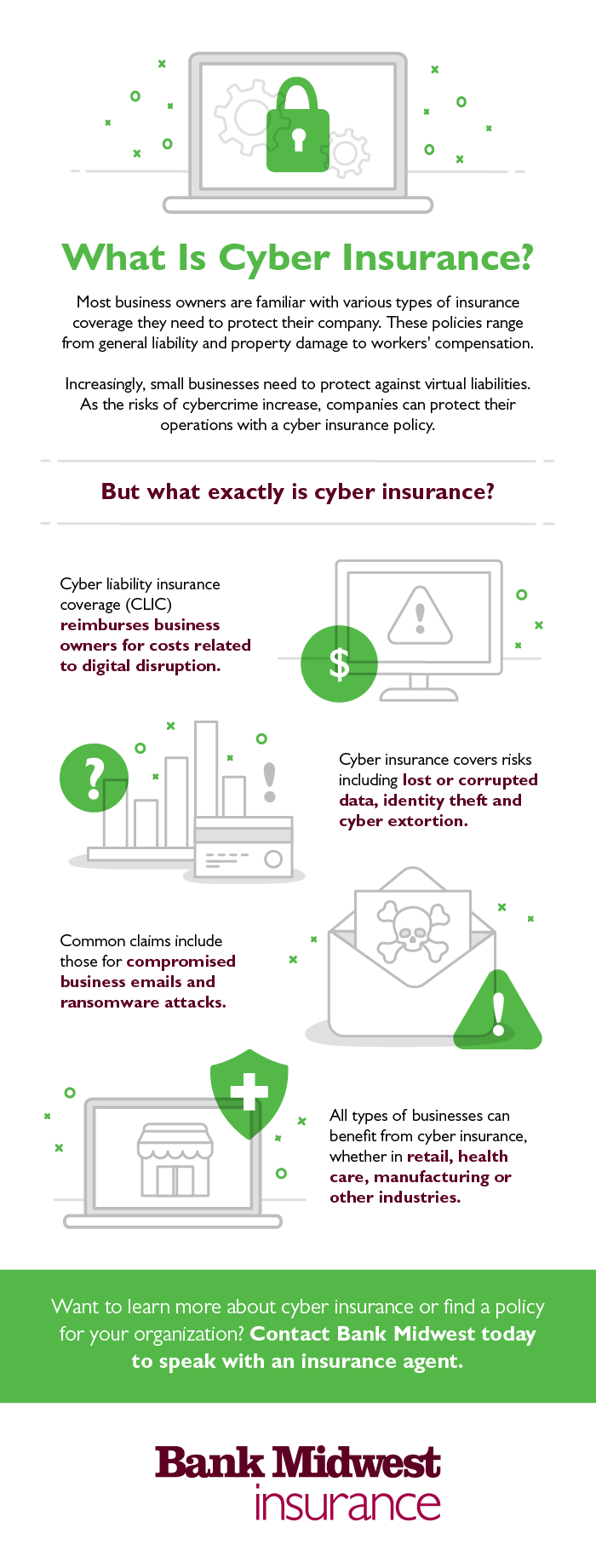
What is cyber insurance?
A cyber insurance policy – also called cyber risk insurance or cyber liability insurance coverage – protects your company against cyber incidents. Risks covered usually include:
- Lost or corrupted data.
- Business interruption.
- Identity theft.
- Cyber extortion.
- Reputation recovery.
- Notification expenses.
A standard business owners policy (BOP) may provide some coverage for certain cyber incidents, III explained. But a dedicated cyber insurance policy is the best way to protect yourself against the vast range of online risks that businesses face.
Who needs cyber insurance?
Most businesses need cyber insurance. Regardless of the size of your organization, there are countless ways hackers can cause damage to your company.
Big-name companies getting hacked may make compelling headlines, but small businesses are just as at risk of being targeted. Verizon’s 2019 Data Breach Investigations Report showed that 43% of breaches involve small business victims.
Small businesses may not have the assets of a large organization, but they have sensitive information that hackers can leverage. Plus, smaller organizations are less likely to have robust security measures, making them easy targets.
What are the most common cyber insurance claims?
According to AIG, the most common types of cyber claims filed are:
1. Business email compromise: 23% of claims
What they are: Scams carried out by email. Common targets are people in finance or payroll departments, according to a security researcher writing for Entrepreneur.
How to avoid them: Educate employees about red flags, such as mismatched “reply-to” and “from” email addresses, or odd requests that don’t seem legitimate.
2. Ransomware: 18% of claims
What they are: Hackers encrypt a business’ sensitive data, making it impossible for owners to carry out operations. Criminals demand payment in exchange for restored access – though there’s no guarantee they’ll uphold their end of the deal.
How to avoid them: Backup your data; hackers won’t have leverage if you still have the information. Additionally, train employees on signs of fraudulent activities, such as clickbait or malicious emails from unknown senders.
3. Data breach by hackers: 14% of claims
What they are: Hackers may use a number of tactics, including taking advantage of network vulnerabilities, using social engineering and more.
How to avoid them: Educate employees on best practices for engaging online. That includes using strong passwords, avoiding suspicious-looking links and not sharing sensitive information over email.
4. Data breach by employee negligence: 14% of claims
What it is: Human error leads to a data breach, such as mistakenly sending data to the wrong person or misplacing a laptop or other device containing sensitive information.
How to avoid it: Again, education is key. Train employees on best practices and make them aware of how mistakes can lead to serious consequences.
How cyber insurance benefits your customers
Cyber insurance protects businesses from financial loss after an incident. But, the benefits directly impact customers, too.
In case of a data breach, cyber insurance will help you notify customers of the incident – a legal requirement in several states. It can also cover credit monitoring services to customers impacted by a breach.
Additionally, customers can be confident that their personal and payment information is secure.
There are many different types of commercial insurance available to business owners. Cyber insurance is one layer of protection. When it comes to getting the right type of business insurance, you must first start with assessing the risks your business is vulnerable to.
To help you determine what insurance coverage your business needs and how your business can benefit from this type of policy contact an experienced insurance agent at Bank Midwest.
OR
REQUEST A QUOTE
Post updated. Originally published July 2020.

